Prerequisites
-
An up-and-running Amazon RDS for SQL Server instance. Instructions for creating a Amazon RDS for SQL Server destination are outside the scope of this tutorial; our instructions assume that you have an instance up and running. For help getting started with Amazon RDS for SQL Server, refer to AWS’s documentation.
Step 1: Verify your Stitch account's data pipeline region
First, you’ll log into Stitch and verify the data pipeline region your account is using. Later in this guide, you’ll need to grant Stitch access by whitelisting our IP addresses.
The IP addresses you’ll whitelist depend on the Data pipeline region your account is in.
- Sign into your Stitch account, if you haven’t already.
- Click User menu (your icon) > Edit User Settings and locate the Data pipeline region section to verify your account’s region.
-
Locate the list of IP addresses for your region:
Keep this list handy - you’ll need it later.
Step 2: Configure database connection settings
In this step, you’ll configure the database server to allow traffic from Stitch to access it. There are two ways to connect your database:
- A direct connection will work if your database is publicly accessible.
- An SSH tunnel is required if your database isn’t publicly accessible. This method uses a publicly accessible instance, or an SSH server, to act as an intermediary between Stitch and your database. The SSH server will forward traffic from Stitch through an encrypted tunnel to the private database.
Click the option you’re using below and follow the instructions.
For Stitch to successfully connect with your database instance, you’ll need to add our IP addresses to the appropriate Security Group via the AWS management console.
Security Groups must reside in the same VPC as the instance. Use the instructions below to create a security group for Stitch and grant access to the VPC.
- Log into your AWS account.
- Navigate to the Security Group Management page, typically Services > Compute > EC2.
- Click the Security Groups option, under Network & Security in the menu on the left side of the page.
- Click Create Security Group.
- In the window that displays, fill in the fields as follows:
- Security group name: Enter a unique name for the Security Group. For example:
Stitch - Description: Enter a description for the security group.
- VPC: Select the VPC that contains the database you want to connect to Stitch. Note: The Security Group and database must be in the same VPC, or the connection will fail.
- Security group name: Enter a unique name for the Security Group. For example:
- In the Inbound tab, click Add Rule.
- Fill in the fields as follows:
- Type: Select
Custom TCP Rule - Port Range: Enter the port your database uses. (
5432by default) - CIDR, IP or Security Group: Paste one of the Stitch IP addresses for your Stitch data pipeline region that you retrieved in Step 1.
- Type: Select
- Click Add Rule to add an additional Inbound rule.
-
Repeat steps 6-8 until all the IP addresses for your Stitch data pipeline region have been added.
This is what a Security Group using Stitch’s North America IP addresses looks like:
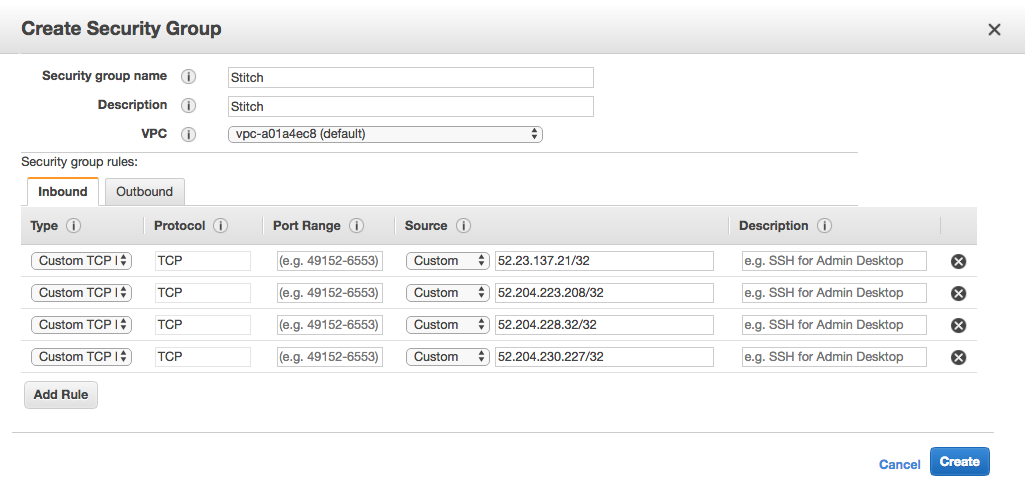
- When finished, click Create to create the Security Group.
- Follow the steps in the Setting up an SSH Tunnel for a database in Amazon Web Services guide to set up an SSH tunnel for Amazon RDS for SQL Server.
- Complete the steps in this guide after the SSH setup is complete.
Step 3: Create a Stitch Amazon RDS for SQL Server database user
In the following tabs are the instructions for creating a Stitch Amazon RDS for SQL Server database user and explanations for the permissions Stitch requires.
-
If you haven’t already, connect to your Amazon RDS for SQL Server instance using your SQL client.
-
Navigate to the
masterdatabase. -
In the
masterdatabase, run the following commands to create a login and a user namedstitch. Replace<STRONG_PASSWORD_HERE>with a strong password:CREATE LOGIN stitch WITH PASSWORD = '<STRONG_PASSWORD_HERE>'; CREATE USER stitch FOR LOGIN stitch; -
Next, navigate to the database where you want Stitch to load data.
-
In this database, run the following commands to create a login and a database user named
stitch. Replace<DATABASE_NAME>with the name of the database:CREATE USER stitch FOR LOGIN stitch; GRANT CONTROL ON DATABASE::<DATABASE_NAME> to stitch; -
Run the following commands to allow the user to create tables and schemas:
GRANT CREATE TABLE ON DATABASE::<DATABASE_NAME> to stitch; GRANT CREATE SCHEMA ON DATABASE::<DATABASE_NAME> to stitch;
In the table below are the database user privileges Stitch requires to connect to and load data into Amazon RDS for SQL Server.
| Privilege name | Reason for requirement |
| CONTROL |
Required to create the necessary database objects to load and store your data. The |
| CREATE TABLE |
Required to create tables in the database. |
| CREATE SCHEMA |
Required to create schemas in the database. |
Step 4: Connect Stitch
To complete the setup, you need to enter your Amazon RDS for SQL Server connection details into the Destination Settings page in Stitch.
Step 4.1: Enter connection details into Stitch
- If you aren’t signed into your Stitch account, sign in now.
-
Click the Destination tab.
- Locate and click the Amazon RDS for SQL Server icon.
- Fill in the fields as follows:
Step 4.2: Define SSH connection details
If you’re using an SSH tunnel to connect your Amazon RDS for SQL Server database to Stitch, you’ll also need to define the SSH settings. Refer to the Setting up an SSH Tunnel for a database in Amazon Web Services guide for assistance with completing these fields.
- Click the Encryption Type menu.
-
Select SSH to display the SSH fields.
-
Fill in the fields as follows:
-
Remote Address: Paste the Public DNS of the SSH sever (EC2 instance) into this field. Refer to the Amazon SSH guide for instructions on retrieving this info.
-
SSH Port: Enter the SSH port of the SSH server (EC2 instance) into this field. This will usually be
22. -
SSH User: Enter the Stitch Linux (SSH) user’s username.
-
Step 4.3: Define SSL connection details
Check the Connect using SSL checkbox. Note: The database must support and allow SSL connections for this setting to work correctly.
Step 4.4: Save the destination
When finished, click Check and Save.
Stitch will perform a connection test to the Amazon RDS for SQL Server database; if successful, a Success! message will display at the top of the screen. Note: This test may take a few minutes to complete.
| Related | Troubleshooting |
Questions? Feedback?
Did this article help? If you have questions or feedback, feel free to submit a pull request with your suggestions, open an issue on GitHub, or reach out to us.